CRTP: My Experience
Hey everyone,
I’m really happy to share that I’ve cleared the CRTP (Certified Red Team Professional) exam on my first attempt! This was a whole new area for me—no prior Active Directory (AD) pentesting experience, and still, I managed to get through it. So if you’re someone wondering whether this cert is possible without an AD background—yes, it is. Let me walk you through how I did it.
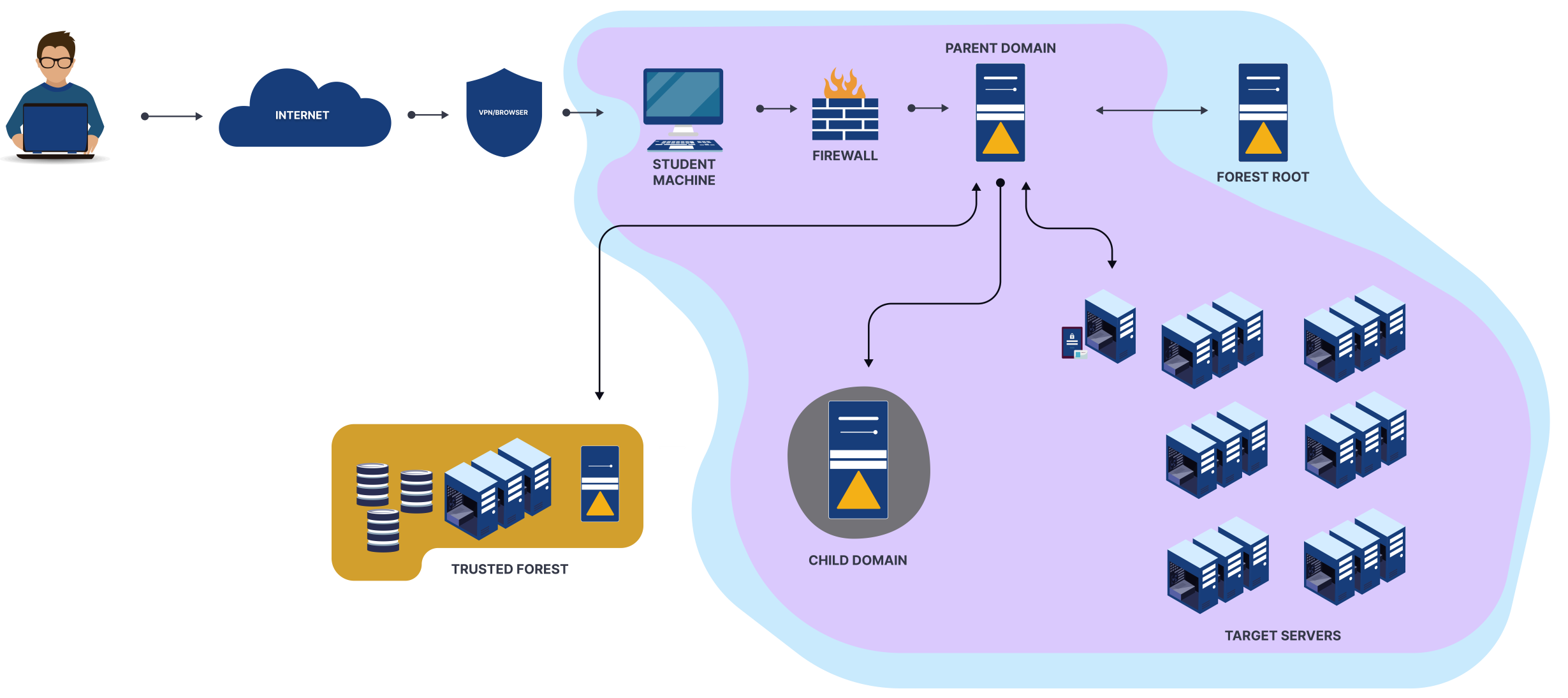
My Background Before CRTP
Before jumping into CRTP, my only real exposure to pentesting was TryHackMe rooms and clearing the eJPT exam. To be honest, I had never done any complete AD-based CTFs before. CRTP was the first time I was diving into the world of Windows domains and enterprise-style networks.
Preparation Strategy
The course content by Altered Security is actually very well-structured and crystal clear. Here’s how I approached it.
I listened to the entire course once without taking any notes—just to absorb the flow. Then, I went back, watched it again, and took detailed notes. After that, I tried to solve everything using only my notes, occasionally referring back to the videos for confirmation. I repeated this pattern whenever I got time—no labs outside this, no extra CTFs—just the course and my notes.
One thing I genuinely wished for during the learning process is that Altered Security could have included hands-on video course with Sliver C2. Sliver is a modern and powerful red team command-and-control framework that’s becoming a solid alternative to Cobalt Strike. It would’ve been really useful to see how it integrates into AD attacks or post-exploitation workflows alongside the traditional tools used in the course. Hopefully, they’ll consider adding it in future course updates.
That’s all I did before scheduling the exam.
Exam Experience
I started my exam on Friday evening at 6 PM and finished it by Saturday morning 10 AM. Yes, I went the full 16 hours straight without a break. I’m someone who works better during the night, so that time window suited me best.
Now, about the difficulty—it was harder than I expected. Even with good preparation, I had to think a lot, test ideas, and keep pushing through.
I got privilege escalation on the first machine within 3 minutes. That gave me a confidence boost. But after that, it took me around 3 hours to find the next escalation path. From there, it was a mix of solving parts step-by-step, some fast, some slow, but overall manageable with persistence.
Reporting and Certification Timeline
After completing the hands-on part, I spent the next day preparing and submitting my final report within 24 hours. I submitted the report on time and received my results on the 8th day, including weekends.
And the very next day after the results, I got my official CRTP certificate.
Final Thoughts
This certification definitely pushes your thinking. It’s not just about running tools—it’s about chaining concepts together, understanding Windows internals, and documenting everything cleanly.
You can view my CRTP certificate here:
To anyone considering CRTP, I’ll say this: You don’t need to be an expert. You just need to be consistent. Watch the course, take notes, practice within the lab, and go for it when you’re ready.
I hope my experience helps you gain some clarity if you’re on the fence. Feel free to reach out to me on if you have any questions—I’ll try my best to help you out.
Best of luck and happy hacking!